Watchguard Ssl Vpn For Mac

Dec 29, 2016 We purchased a watchguard firewall and have installed the SSLVPN client on a bunch of our macbook pros. Works great for the most part. Have one Sierra machine that gives the fol. Watchguard SSL VPN client on Mac OS X 10.12 (Sierra) - Spiceworks. The IKEv2 VPN offers the highest level of security of the mobile VPNs available on the Watchguard firewall. This VPN option includes multi-layer security, and supports certificate-based client authentication instead of a pre-shared key.
- Watchguard Mobile Vpn With Ssl Client
- Watchguard Vpn Client For Mac
- Watchguard Ssl Vpn Client Download
Compatibility Guide WatchGuard XTM, Firebox and any other appliance which have configurable RADIUS authentication are supported. For example, WatchGuard Mobile VPN with SSL. Before proceeding, please ensure you have the following:. account. Computer virtualization software such as or. Virtual Machine requirements:.
1024 MB RAM. 8 GB disk size If you have already created a LoginTC domain for your LoginTC RADIUS Connector, then you may skip this section and proceed to. to LoginTC Admin. Click Domains:. Click Add Domain:.
Enter domain information: Name Choose a name to identify your LoginTC domain to you and your users Connector RADIUS. the latest LoginTC RADIUS Connector. Unzip the file. Import the Open Virtualization Format (OVF) file into your computer virtualization software.
Ensure that the LoginTC RADIUS Connector has a virtual network card. Start the virtual appliance. You will be presented with a console dashboard:. The first thing you must do is set the logintc-user password:. By default the appliance network is configured by DHCP. If you wish to manually configure the network, use the Down arrow key to navigate to Network Configuration and DNS Configuration.
For access to the web interface select Web Server and then Start: It may take 30-60 seconds to start the first time:. Once started, access the web interface by navigating to the URL mentioned in the information box: The LoginTC RADIUS Connector runs 6.5 with. A firewall runs with the following open ports: Port Protocol Purpose 22 TCP SSH access 1812 UDP RADIUS authentication 1813 UDP RADIUS accounting 8888 TCP Web interface 80 TCP Package updates (outgoing).
Note: Username and Password logintc-user is used for SSH and web access. The default password is logintcradius. You will be asked to change the default password on first boot of the appliance and will not be able to access the web interface unless it is change.
The logintc-user can run sudo su to become the root user. Configuration describes how the appliance will authenticate your -speaking device with an optional first factor and LoginTC as a second factor. Each configuration has 4 Sections: 1.
LoginTC This section describes how the appliance itself authenticates against with your LoginTC organization and domain. Only users that are part of your organization and added to the domain configured will be able to authenticate. First Factor This section describes how the appliance will conduct an optional first factor. Either against an existing LDAP, Active Directory or RADIUS server. If no first factor is selected, then only LoginTC will be used for authentication (since there are 4-digit PIN and Passcode options that unlock the tokens to access your domains, LoginTC-only authentication this still provides two-factor authentication).
Passthrough This section describes whether the appliance will perform a LoginTC challenge for an authenticating user. The default is to challenge all users.
However with either a static list or Active Directory / LDAP Group you can control whom gets challenged to facilitate seamless testing and rollout. Client and Encryption This section describes which -speaking device will be connecting to the appliance and whether to encrypt API Key, password and secret parameters.
Data Encryption It is strongly recommended to enable encryption of all sensitive fields for both PCI compliance and as a general best practice. The web interface makes setting up a configuration simple and straightforward.
Each section has a Test feature, which validates each input value and reports all potential errors. Section specific validation simplifies troubleshooting and gets your infrastructure protected correctly faster. Close the console and navigate to your appliance web interface URL. Use username logintc-user and the password you set upon initial launch of the appliance.
You will now configure the LoginTC RADIUS Connector. Create a new configuration file by clicking + Create your first configuration: Configure which LoginTC organization and domain to use: Configuration values: Property Explanation apikey The 64-character organization API key domainid The 40-character domain ID The API key is found on the LoginTC Admin page. The Domain ID is found on your domain settings page. Click Test to validate the values and then click Next: Configure the first authentication factor to be used in conjunction with LoginTC. You may use Active Directory / LDAP or an existing RADIUS server. You may also opt not to use a first factor, in which case LoginTC will be the only authentication factor.
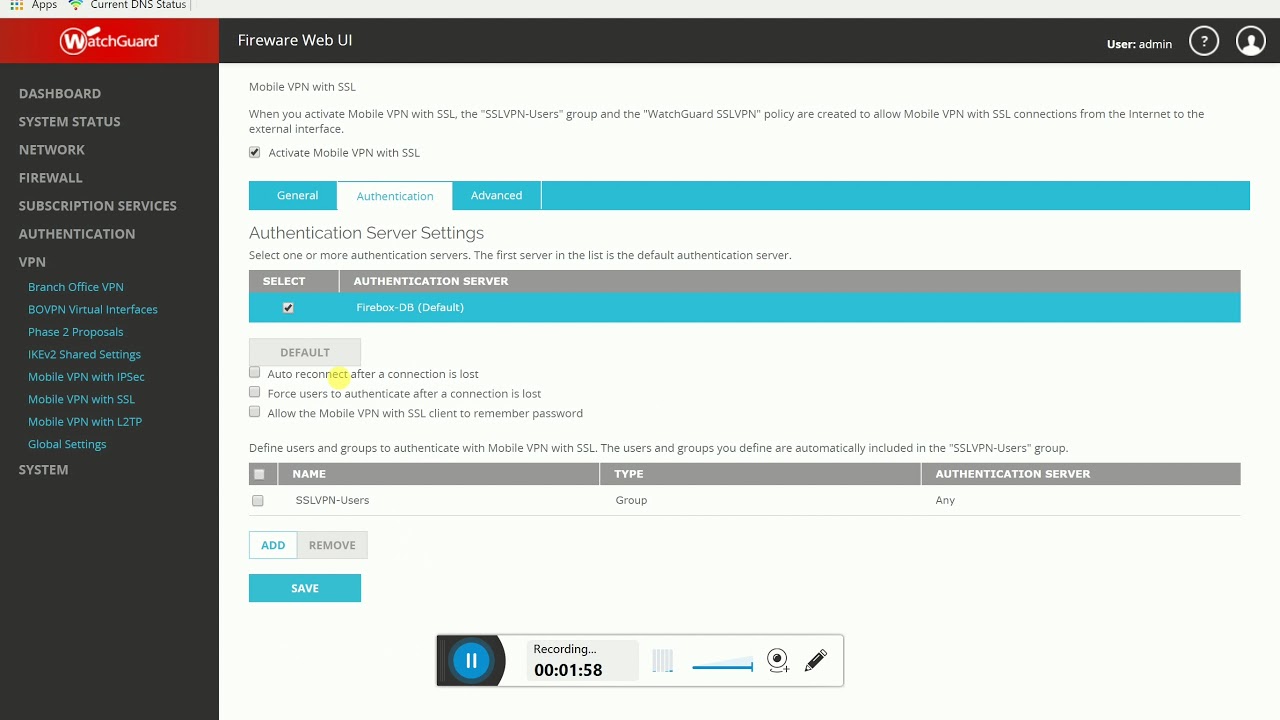
Select Active Directory if you have an AD Server. In order to use Mobile VPN with SSL, you must properly configure the Group Attribute in your RADIUS Connector. WatchGuard devices use the Group Attribute value to set the attribute that carries the User Group information. This information is used for access control.
To match WatchGuard’s default values, set RADIUS Group Attribute to Filter-Id and LDAP Group to SSLVPN-Users LDAP Group / AD Group: The name of a group in the LDAP Directory that all authenticating users belong to. The group name must also be added to WatchGuard’s list of groups authorized to authenticate using SSL. By default this is only the SSLVPN-Users group, but other groups can be added manually from the WatchGuard Web UI.
Mobile VPN with IPsec doesn't use the Group Attribute when authenticating users. You can either select None, or if you choose to specify a Group Attribute, the values won't affect users connecting with IPsec.
Note: If you want to enable users to connect with multiple policies in addition to IPsec (SSL, L2TP, etc.) the Group Attribute values may need to be specified based on other policies. Click Test to validate the values and then click Next. If you want to use your existing RADIUS server, select RADIUS: Configuration values: Property Explanation Examples host Host or IP address of the RADIUS server radius.example.com, 192.168.1.43 port (optional) Port if the RADIUS server uses non-standard (i.e., 1812) 6812 secret The secret shared between the RADIUS server and the LoginTC RADIUS Connector testing123. RADIUS Vendor-Specific Attributes Common Vendor-Specific Attributes (VSAs) found in the FreeRADIUS dictionary files will be relayed. Click Test to validate the values and then click Next. Configure which users will be challenged with LoginTC.
This allows you to control how LoginTC will be phased in for your users. This flexibility allows for seamless testing and roll out. For example, with smaller or proof of concept deployments select the option. Users on the static list will be challenged with LoginTC, while those not on the list will only be challenged with the configured.
That means you will be able to test LoginTC without affecting existing users accessing your VPN. For larger deployments you can elect to use the option.
Only users part of a particular LDAP or Active Directory Group will be challenged with LoginTC. As your users are migrating to LoginTC your LDAP and Active Directory group policy will ensure that they will be challenged with LoginTC. Users not part of the group will only be challenged with the configured. Select this option if you wish every user to be challenged with LoginTC.
Select this option if you wish to have a static list of users that will be challenged with LoginTC. Good for small number of users. LoginTC challenge users: a new line separated list of usernames. For example: jane.doe jane.smith john.doe john.smith Select this option if you wish to have only users part of a particular Active Directory or LDAP group to be challenged with LoginTC. Good for medium and large number of users.
Configuration Simplified If was selected in the non-sensitive values will be pre-populated to avoid retyping and potential typos. Click Test to validate the values and then click Next. Configure RADIUS client (e.g. your RADIUS-speaking VPN): Client configuration values: Property Explanation Examples name A unique identifier of your RADIUS client CorporateVPN ip The IP address of your RADIUS client (e.g. your RADIUS-speaking VPN) 192.168.1.44 secret The secret shared between the LoginTC RADIUS Connector and its client bigsecret authentication The authentication factors (comma-separated) ldap,logintc, radius,logintc, or logintc. Data Encryption It is strongly recommended to enable encryption of all sensitive fields for both PCI compliance and as a general best practice. Click Test to validate the values and then click Save.
When you are ready to test your configuration, create a LoginTC user (if you haven’t already done so). The username should match your existing user. Provision a token by following the steps:. In a new tab / window to LoginTC Admin. Click Domains. Click on your domain.
Click on Members. Click Issue Token button beside your user:. A 10-character alphanumeric activation code will appear beside the user:. Open the LoginTC mobile app. Enter the 10-character alphanumeric activation code:. Lock the token with a PIN or passcode: When you have loaded a token for your new user and domain, navigate to your appliance web interface URL: Click Test Configuration: Enter a valid username and password; if there is no password leave it blank. A simulated authentication request will be sent to the mobile or desktop device with the user token loaded.
Approve the request to continue: Congratulations! Your appliance can successfully broker first and second factor authentication. The only remaining step is to configure your RADIUS device!
If there was an error during testing, the following will appear: In this case, click See logs and then click the /var/log/logintc/authenticate.log tab to view the log file and troubleshoot: Once you are satisfied with your setup, configure your WatchGuard to use the LoginTC RADIUS Connector. For your reference, the appliance web interface Settings page displays the appliance IP address and RADIUS ports: The following are quick steps to get VPN access protected with LoginTC. The instructions can be used for existing setups as well. Although these were performed on WatchGuard Fireware XTM Web UI, the same is true for other devices in the XTM series. Select which Mobile VPN protocol to use in your configuration. Property Explanation Example IP Address Address of LoginTC RADIUS Connector 10.0.10.130 Port RADIUS authentication port. Must be 1812.
1812 Passphrase The secret shared between the LoginTC RADIUS Connector and its client bigsecret Confirm The secret shared between the LoginTC RADIUS Connector and its client bigsecret Timeout Amount of time in seconds to wait. At least 60s. 60 Retries Amount of times to retry authentication. 1 Group Attribute RADIUS Attribute to be populated with user group info.
Must be 11 when using SSL. 11 Dead Time Amount of time an unresponsive RADIUS server is marked as inactive 10.
Group Attribute and Access Control WatchGuard devices can use the Group Attribute value to set the attribute that carries the User Group information. This information is used for access control by certain VPN protocols. However, Mobile VPN with IPsec does not use the Group Attribute. The value won’t affect users connecting with IPsec. If you are using multiple VPN protocols (such as SSL) then you may need to set the value to match their requirements. You can also configure the to provide failover. This prevents the RADIUS Server from dropping authentication requests if it goes offline or receives too many requests.
Click Save. Click VPN:. Under VPN click Mobile VPN with IPsec. Click Add to create a new group.
Watchguard Mobile Vpn With Ssl Client
Note that the name of the group does not have to match any of the groups names in the LDAP Directory. In General Settings, complete the form and select RADIUS as the authentication server. Property Explanation Example Name A unique name for this group configuration. Does not have to match any of the existing groups in the LDAP Directory. Office VPN Authentication Server The type of device that users of this group will be authenticated with. Radius Passphrase The secret shared between the Mobile VPN client and the RADIUS server. The secret must be provided to all IPsec users.
Sharedsecret Confirm The secret shared between the Mobile VPN client and the RADIUS server. Sharedsecret Primary Primary IP address or domain name Firebox users connect to. 10.0.10.130 Backup (optional) Secondary IP address or domain name Firebox users connect to. 10.0.10.131.
Fill out the forms under the IPsec Tunnel, Resources, and Advanced tabs to match the settings of your client. For more information about IPsec client configurations, check the.
Click Save You are now ready to test your configuration. To test, navigate to your WatchGuard clientless VPN portal or use a WatchGuard client and attempt access.
To test SSL connections, you can use the following online portal: interface IP address/sslvpnlogon.shtml To test IPsec connections, use an IPsec VPN client such as the WatchGuard Mobile Application. There are several options for managing your users within LoginTC:. Individual users can be added manually in.
Bulk operations in. Programmatically manage user lifecycle with the. One-way user synchronization of users to LoginTC Admin is performed using. WatchGuard devices have built-in settings that make it easy to configure a secondary RADIUS server to provide failover. — To set up another RADIUS server, deploy the downloaded LoginTC Connector again (you can deploy it multiple times) and configure it using the same settings as the first one.
To review the Connector configuration process. Afterwards, login to your WatchGuard Web UI and make the following changes:. Select Authentication from the left-hand navigation bar. Click Servers.
Select RADIUS. Check the box to Enable Secondary RADIUS Server. Complete the Secondary Server Settings Form using the same settings as the primary one Property Explanation Example IP Address Address of Secondary LoginTC RADIUS Connector 10.0.10.131 Port RADIUS authentication port. Must be 1812.
1812 Passphrase The secret shared between the LoginTC RADIUS Connector and its client newsecret Confirm The secret shared between the LoginTC RADIUS Connector and its client newsecret Timeout Amount of time in seconds to wait. At least 60s.
Watchguard Vpn Client For Mac
120 Retries Amount of times to retry authentication. 1 Group Attribute RADIUS Attribute to be populated with user group info. Email Support For any additional help please email support@cyphercor.com.
Watchguard Ssl Vpn Client Download
Expect a speedy reply. If you are using a Mobile VPN protocol such as SSL and are unable to authenticate, check that your Group Attributes are configured correctly. Navigate to your WatchGuard Web UI and click Dashboard in the left-hand navigation bar: Click on Traffic Monitor: Select Diagnostic from the table header options: If you can find the following error message then there is a problem with your Group Attribute settings: 2015-XX-XX 16:52:41 admd Authentication failed: user username@RADIUS isn't in the authorized SSLVPN group/user list! Search for the following error message: 2015-XX-XX 16:59:52 admd RADIUS: no attribute-value pair is retrieved from packet If found, it means that the RADIUS Connector is not sending back any Group Attribute information.
Navigate to your appliance web interface and click Configurations. Select the domain you’re having problems with: Click the Edit Button in the First Factor section: Scroll down to the to the Group Attribute section:. If “None” is selected, change it to “Specify a group attribute”. To review how to configure the Group Attribute for SSL. Otherwise, check that your user is a member of the specified group in the LDAP Directory. If they are not, it will cause RADIUS to return a blank attribute.
If you find a log message similar to this: 2015-XX-XX 16:52:41 admd RADIUS: finished parsing attribute-value pairs 2015-XX-XX 16:52:41 admd RADIUS: group 1, type=11 value=L2TP-Users 2015-XX-XX 16:52:41 admd RADIUS: retrieve VP:Filter-Id(11) int=10 Then the RADIUS server is sending back a Group Attribute, but it may not be the correct one. Check that the value is the name of the group that has been added to list of groups authorized to authenticate with SSL. Log into the WatchGuard Web UI and select VPN from the left-hand navigation bar. Click on Mobile VPN with SSL: Click on the Authentication tab: The bottom table contains the list of groups that are authorized to connect with SSL. If the group returned by the RADIUS server is not part of it, it must be added.
Click the Add button: Type in the group name and select RADIUS as the Authentication Server: If authentication is failing, it is possible that the authentication requests are timing out too quickly. By default, LoginTC push requests will timeout after 60 seconds. Another timeout value is defined by the RADIUS server configuration.
If it is set too low, it will cause requests to prematurely timeout. To check, login to your WatchGuard Web UI. Select Authentication from the left-hand navigation bar, then click Servers.
Click RADIUS. Check the Timeout attribute field. It should be at least 60 seconds. If you have LoginTC RADIUS Connector 1.1.0 or higher, follow these instructions to upgrade your LoginTC RADIUS virtual appliance to the latest version (2.1.1):. SSH into the virtual appliance or open the console (use same username / password as web GUI). cd /tmp. curl -O (SHA‑1: 8b37911283cce9fce9efe4e628dfdb).
tar -xf logintc-radius-connector-2.1.1-upgrade.tar.gz. sudo sh logintc-radius-connector-2.1.1-upgrade/upgrade.sh.
